Compromising digital assets, disrupting daily operations, or exfiltrating sensitive data are among the most severe consequences of a breach, a prospect that sends shivers down the spines of many CISOs. What adds to this daunting reality is the staggering cost of data breaches, with the global average reaching $4.35 million in 2022.
As soon as threat actors gain privileged access to our infrastructure and we become aware of it, containing the breach becomes our top priority. Nevertheless, recovering full control without completely restoring compromised systems and data poses a significant hurdle, as does identifying the root cause and ensuring that threat actors do not retain access.
In this article, we will delve into the impact of breaches on organizations, explore how to establish the initial breach scope using Maltego, and share a downloadable playbook for investigating potential breaches with Maltego.
The True Impact of Data Breaches on an Organization 🔗︎
A data breach is one of the most severe events an organization might face as it often triggers high-impact incidents.
These range from compromising business or customer data, including sensitive personal information such as addresses, phone numbers, credit cards, and bank accounts, to data privacy concerns like profiling individuals based on religion, sexual orientation, or political interests.
For global companies, data breaches could involve datasets with thousands or millions of customers from different regions, leading to two major concerns:
- Reputational: How a company manages communication and responds to affected individuals and agencies will likely determine how the public perceives their diligence in addressing the issue. Sometimes even small details about the root cause, such as inadequate security measures, can greatly influence how others view the company’s trustworthiness in the future, and restoring that trust can become a daunting task.
- Regulatory: Breaches in critical infrastructure, or those affecting a large volume of sensitive PII data, require immediate disclosure to regulators. Depending on the incident’s management and data type, sanctions can range from hundreds of thousands to millions.
How to Identify a Data Breach 🔗︎
Data breaches can affect companies differently, so various teams within your organization should stay on the lookout for early signs or indicators that require verification. There are several triggers to watch out for:
- Third-party notifications: Follow alerts about data, such as stolen credentials, found during a criminal investigation revealed by national Computer Security Incident Response Teams (CSIRTs) or intelligence agencies.
- Infosec vendor or threat intelligence reporting service warnings: These may indicate threats that have impacted your organization or similar ones in your industry or country. For example, financial institutions in Mexico being targeted by a threat actor.
- Alerts about criminal activity: Your threat intelligence team may detect discussions about your organization in the dark web or hacking/criminal forums, including the sale of access or stolen data.
- Suspicious security events: Your SOC team may detect activities related to sensitive users or environments, such as active directories, or a significant number of systems communicating with an external system that could be linked to criminal infrastructure.
- Relevant techniques, tactics, and procedures (TTPs) or indicators of compromise (IOCs): Your threat hunting team may discover well-known threat actor patterns in your systems while analyzing the threat landscape.
If you want to find out how to investigate a potential breach in Maltego, download the playbook now!
How to Determine the Extent of a Breach 🔗︎
Whether using Maltego or other relevant tools, your cybersecurity teams can conduct a set of activities to assess the extent and severity of the breach.
Here’s what we recommend as starting points:
- Triage and collect artifacts to generate an initial set of IOCs for investigation.
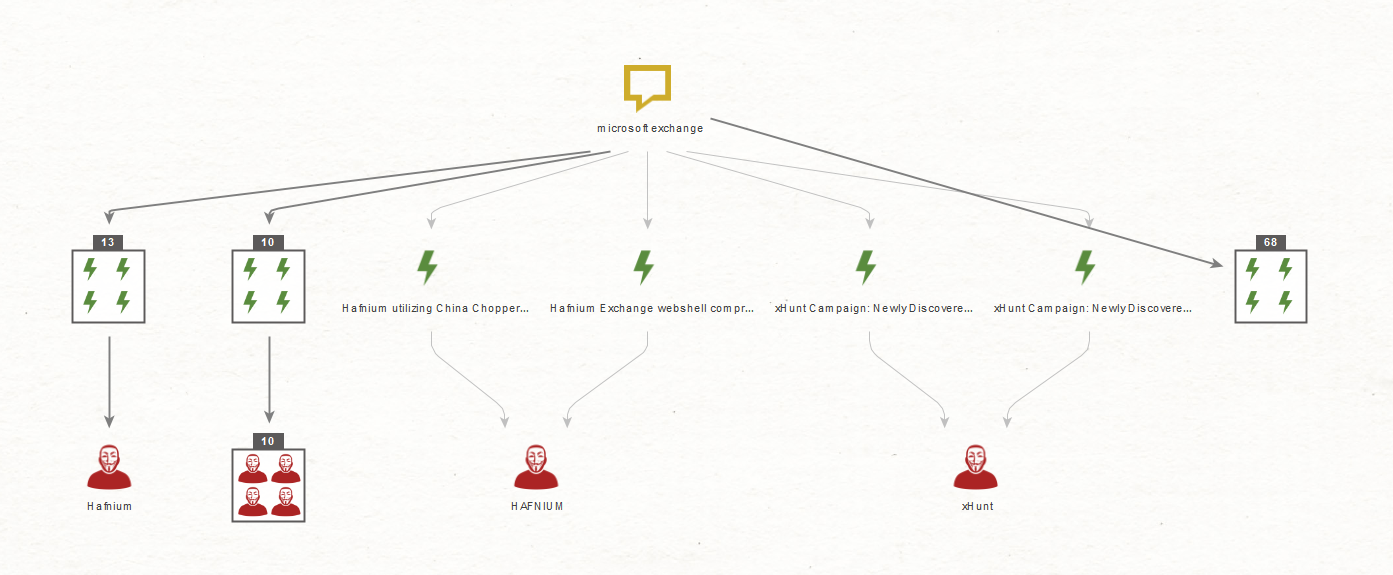
- Obtain threat intelligence from current IOCs to identify ongoing campaigns and attribute them to well-known threat actors.
- Perform threat hunting over the endpoint/network infrastructure to gauge the number of impacted systems.
- Conduct lateral movement analysis to trace how the attacker moved between systems.
- Engage in forensic analysis of the top compromised systems to gain insights into the attacker’s TTPs.
- Analyze exfiltration to understand potential access to data and identify remarkable outbound data flows.
- Monitor the dark web and other criminal data sources to identify any potential activities related to selling access or data to your infrastructure.
How Maltego Accelerates Your Breach Investigation 🔗︎
As an investigative tool, Maltego enables you to connect to a wide range of data sources through a single interface, saving precious time needed to minimize damage during a potential breach.
Maltego enables you to:
Having the right tools is essential, but preparation is also crucial when dealing with a potential breach. To aid you, we have prepared a free playbook for investigating potential breaches with Maltego. Inside, you will find ready workflows for:
- Performing Incident Triage
- Collecting Threat Intelligence
- Hunting IOCs
- Analyzing Lateral Movement
- Investigating Exfiltration
This playbook is valuable for teams that have already experienced a breach and need to act swiftly with Maltego. It is equally beneficial for infosec professionals who want to simulate and practice their response using fake data.
Download the FREE Playbook for Investigating Data Breaches 🔗︎
Download the resource
Don’t forget to follow us on Twitter, LinkedIn, and Mastodon, and sign up to our email newsletter to stay updated on the latest tutorials, use cases, and webinars!
Happy investigating!
About the Author 🔗︎
Carlos Fragoso
Carlos is the Principal Subject Matter Expert and Lead Instructor at Maltego with over 20 years of professional experience in information security: Incident response, digital forensics, threat intelligence, and threat hunting. A curious and passionate investigator working with big companies and LEAs to tackle cybercrime around the world (Europe, Middle East, LATAM) SANS Institute Instructor.


 4.5 rating
4.5 rating