Security Operations Center (SOC) teams stand on the front lines in cybersecurity, keeping our cyber world safe from endless threats. For these teams, every second counts as they work tirelessly to identify and mitigate cyber threats targeting their organizations.
Balancing a rapid response with thorough initial assessments, all while juggling a myriad of tools, processes, and alerts, is a challenge that the teams face every single day, making efficiency both a goal and a must for survival. This is where the strategic importance of SOC playbooks comes into play.
An Overview of SOC Playbooks 🔗︎
SOC Playbooks are essential for cyber defense, providing clear, step-by-step instructions tailored to various threat scenarios. They serve not merely as documents, but as lifelines that streamline decision-making processes, ensuring that every team member understands their role and actions to take before, during, and after a security incident. Additionally, playbooks facilitate prompt communication with stakeholders in case of a security breach, thereby enhancing transparency and stakeholder relations.
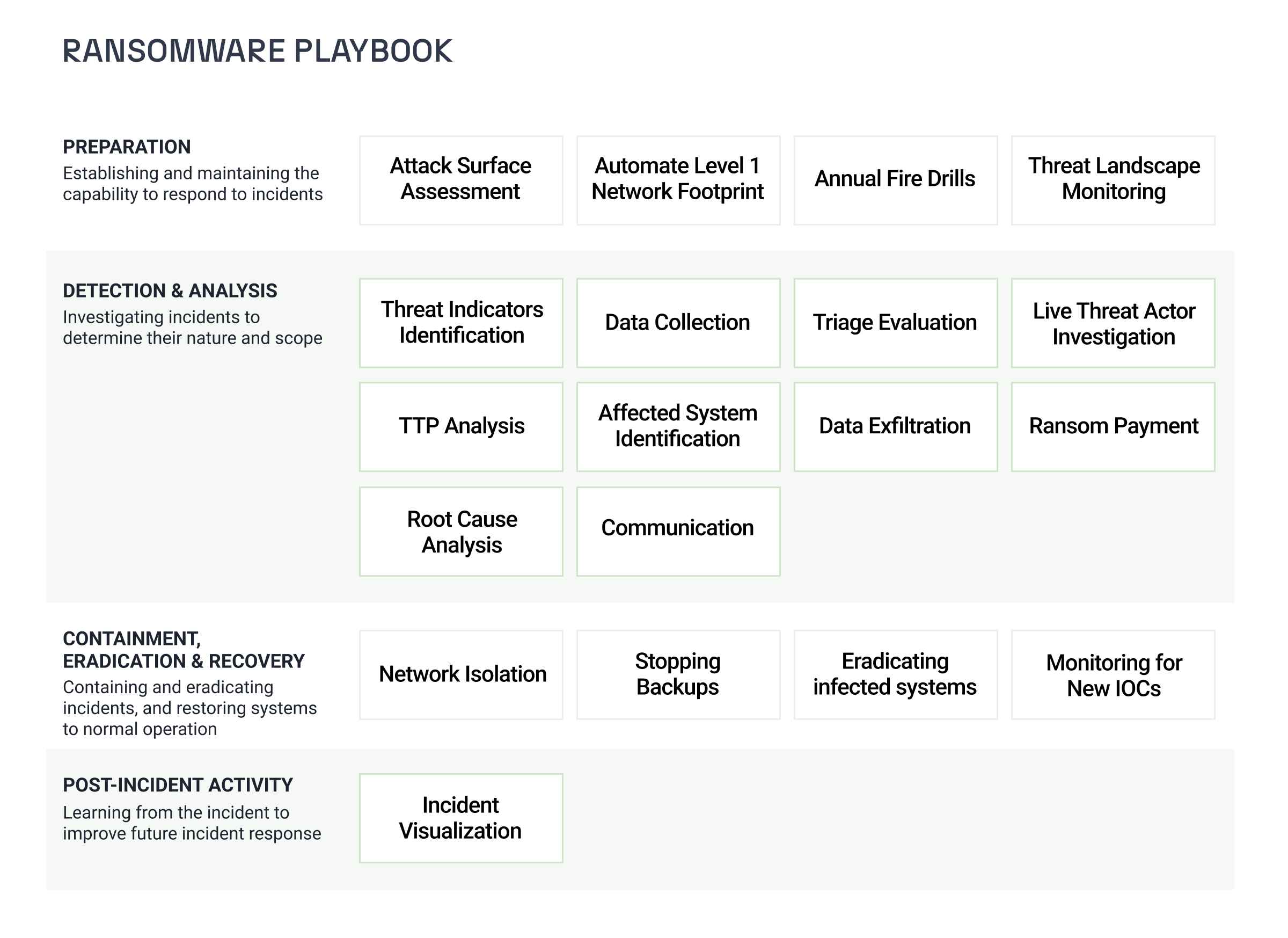
Although no one-size-fits-all format exists for the SOC playbooks, most teams follow the National Institute of Standards and Technology (NIST)’s standards, including the following sections.
INVESTIGATOR NOTE It is important to recognize that not every SOC is involved in every stage of incident response. Often, SOCs serve primarily in initial detection and analysis, assisting with tasks that Computer Security Incident Response Teams (CSIRTs) or Incident Response (IR) teams might later expand upon. Thus, in many instances, SOCs act as the foundational layer of incident response. In some scenarios, the term “SOC” might encompass the entire incident response spectrum, though this broader involvement is less typical. Remember these insights as you tailor playbooks to fit your team’s needs!
- Preparation: Establishing and maintaining the capability to respond effectively to incidents, including developing policies, plans, and procedures, defining roles, training personnel, and acquiring necessary tools and resources.
- Detection & Analysis: Identifying and investigating incidents to determine their nature and scope. This includes monitoring for and analyzing potential incidents, effectively using detection tools, and correctly identifying and documenting incidents.
- Containment, Eradication & Recovery: Limiting the spread of an incident, removing its components, and restoring systems to normal operation. This involves executing a containment strategy, eradicating the incident’s cause, and recovering affected systems and data.
- Post-Incident Activity: Learning from the incident to improve future incident response efforts and overall security posture. This includes conducting a post-incident review, documenting lessons learned, and implementing improvements to policies and controls.
Amplifying SOC Playbooks with Maltego: Ransomware 🔗︎
Security teams are constantly evolving their strategies to respond to and combat the ever-changing cyber threats. Maltego amplifies the SOC playbook’s effectiveness by automating data collection and visualization, turning complex datasets into clear, actionable insights, which saves precious time and helps analysts make informed decisions faster. We will focus on the Detection & Analysis phase, identified as the pivotal segment of the entire process. It is within this phase that Maltego’s capabilities prove most advantageous.
Let’s discuss how Maltego can be used for the ransomware playbook and elevate the SOC operation with the world’s most used cyber investigation platform! For insights into enhancing incident response workflows with Maltego, and to streamline investigative processes, consider delving into the Maltego Handbook for Incident Response.
Ransomware 🔗︎
Maltego enables teams to quickly assess the impact and scope of a ransomware attack and understand the methods through which threat actors control their victims, including uncovering malicious infrastructure such as command and control servers. By speeding up the aggregation and analysis of indicators of compromise (IOCs), Maltego helps identify patterns and connections that might go unnoticed.
Preparation 🔗︎
-
Attack Surface: Perform an attack surface assessment to identify and catalog all externally exposed hosts, including those potentially unknown to the organization. Regularly update the asset list to reflect the current state of the network environment.
-
Automated Level 1 Network Footprint: Efficiently conduct network footprinting with Maltego Machines, saving you considerable time on information gathering, processing, and visualization.
-
Drills: Conduct annual cybersecurity exercises to simulate ransomware attack scenarios. This practice helps validate the effectiveness of the playbook and the organization’s readiness to respond to actual incidents.
-
Threat Landscape Monitoring: Continuously monitor and analyze threat intelligence to stay informed about emerging threats to the organization, industry-specific risks, and evolving ransomware tactics. Incorporate various sources to obtain a comprehensive threat perspective.
Detection and Analysis 🔗︎
- Identify Threat Indicators: Aggregate and analyze indicators from security solutions such as SIEMs like Splunk, AV/EDR, ticketing systems, and notifications from security personnel or users to identify potential ransomware incidents quickly.
- Data Collection: Collect detailed information on indicators like Bitcoin addresses, emails, file hashes, file behaviors, domain reputations, and IP communications. Enrich this data using third-party sources to assess the severity and impact of the threat.
- Triage: Evaluate the impact (e.g., data destruction, proliferation) and scope (e.g., number of affected hosts, additional IOCs) to prioritize response efforts. Determine if the event is a false positive; if yes, stop; if no, proceed with analysis.
- Live Threat Actor: If a live threat actor is identified, utilize Maltego for real-time investigations and support to block new IOCs as they are identified.
- Identify Ransomware Family: Use OpenCTI to identify the ransomware’s TTPs, determine decryption possibilities, and identify the targeted OS. This information aids in tailoring the response strategy.
- Identify Affected Systems Type: Determine the types of affected systems (servers, workstations) using tools like Splunk to understand the attack’s breadth and depth.
- Data Exfiltration: If data exfiltration is suspected, activate the Data Loss Playbook to mitigate and assess the damage.
- Pay the Ransom: Assess the legality and advisability of paying the ransom, acknowledging that not all ransomware threat actors are sanctioned entities, paying criminals is illegal in some jurisdictions and generally discouraged according to Business Continuity Plans (BCPs). Perform a thorough blockchain analysis to fully understand the implications and potential risks associated with a ransom payment.
- Root Cause Analysis: Conduct a thorough analysis to identify the attack’s root cause, which is crucial for preventing future incidents.
- Send Communication: Communicate effectively with all stakeholders throughout the incident to ensure coordinated and informed response actions.
Containment, Eradication, and Recovery 🔗︎
- Network Isolation: Block system-to-system communication to prevent the spread of ransomware. Disconnect affected systems from the network as well as any shared drives. And make sure that threat actors can no longer control the infected systems.
- Stop Backups: Temporarily halt backup processes to prevent backup data encryption. Verify the integrity of the latest stable version of backups and preserve the latest backups with additional security measures.
- Malware Infection: Follow the Malware Playbook to remove ransomware and other implants to remotely control and preserve access from infected systems and prevent reinfection.
- Monitor for New IOCs: Continuously monitor new IOCs and the evolution of TTPs from the same incident or campaign during and after the containment phase to detect any lingering threats or additional points of compromise.
Post-Incident Activity 🔗︎
- Incident Visualization: Use Maltego to create a comprehensive visualization of the incident, depicting the relationships between hosts, IOCs, and the attack’s progression. This visualization aids in understanding the incident’s full scope and can be used for debriefing and lessons learned.
A Brief Investigation in Maltego 🔗︎
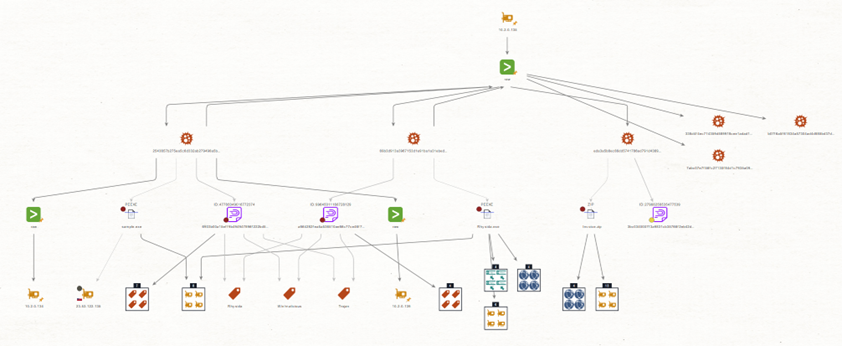
This investigation represents the detection and analysis phase of the ransomware investigation with Maltego. Our starting point is the IPv4 address from the malware sample; Rhysida ransomware.
Step 1: Drop an IPv4 Address and update it with the address of the affected host.
Step 2: Run the Transform Get Malware Attacks Events [Splunk] to identify any malware events associated with the host. Other early unclear events could lead to identifying an infection by investigating suspicious outbound connections. However, in our case, we will focus directly on malware attack events.
Step 3: Select all events Entities and run To FileHash [Hash] to extract the associated hashes. You will see hash Entities as a result.
Step 4: Select the hash Entities and run Lookup by Hash [Polyswarm]. This Hub item is included in the Maltego Selection for CTI.
Step 5. Select the result with the red dot and run the Transform To Tags [Polyswarm] to identify the malware family. This will help verify if there’s a connection to the identified malware.
INVESTIGATOR TIP
To find additional affected hosts, run the Search All Events [Splunk] Transform on the hashes associated with the same Polyswarm Entities.
Step 6: Select the hashes associated with the ransomware and run the Transform To VirusTotal File [VirusTotal Public API] to gather more IoCs.
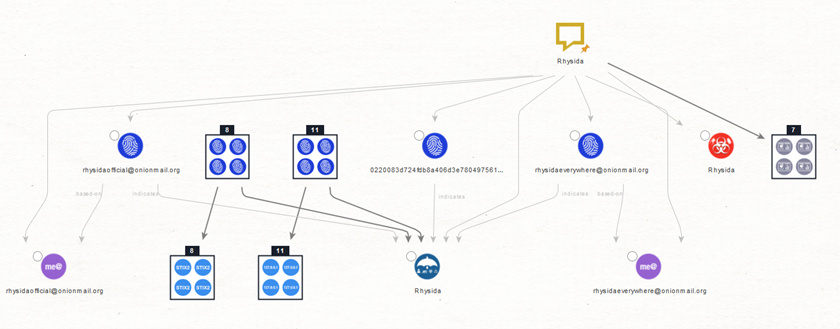
Step 7: Select the file Entities and run To Contacted IP Addresses [VirusTotal Public API] and To Contacted Domains [VirusTotal Public API] Transforms. After this step, if the team wants to know about the malware(Rhysida) as much as possible, they can use the OpenCTI integration on a new graph.
Step 8: Paste the name of the ransomware family as a phrase Entity and run the Transform Search by Phrase [OpenCTI].
Step 9: Select the STIX2 intrusion set and run the Set to Indicators [STIX2].
Step 10: Select all STIX2 indicator Entities and run the Indicator to all Observables [OpenCTI].
Step 11: Check email logs for emails generated from the identified Domains as well as connections made to/from the IP addresses by using the Get All Mail Events [Splunk] Transform.
In our playbooks, we detail the step-by-step process for four widely recognized use cases, making them ready for investigation so you can easily implement them in your Maltego platform.
- Ransomware
- Phishing Attack
- Malware Infection
- Vulnerability Response
- Insider Threats (Data Leakage)
You can also find out about how to enhance the investigations with automation and the benefits of the automation in the playbooks!
Embracing a playbook goes beyond just meeting immediate challenges; it’s about evolving into a constantly adaptive presence against cyber threats. With these playbooks, you can assess your team’s current methods and discover ways to boost efficiency and the direct impact of your operations on the business!
Download SOC Playbooks 🔗︎
Download the resource
As cybersecurity professionals, we are committed to continuously refining our strategies and tools, which is crucial to staying ahead of adversaries. Embracing the synergy between SOC playbooks and Maltego’s capabilities offers a pathway to enhanced security and a more empowered stance in the digital domain. The journey of bolstering our cyber defenses is ongoing, and with a platform like Maltego at our disposal, it’s a journey that we can undertake with greater confidence and success.
To truly understand the immediate impact Maltego can have on your operations and see how it translates into enhanced efficiency for your organization, consider calculating a tailored ROI today.
Happy investigating!
About the Author 🔗︎
Mario Rojas
Mario Rojas is a former Cyber Security and Threat Intelligence Subject Matter Expert at Maltego with more than 14 years of experience in the cybersecurity field. His expertise in open-source intelligence (OSINT) allows him to effectively map and visualize complex relationships and connections between entities, from IP addresses and domain names to social media profiles and Darkweb forums.