In June 2021, the United States Government seized several Iranian sites, including presstv[.]com, claiming that the sites were spreading misinformation across their platforms.
Below, in the lower right corner, you can see the image that welcomes visitors when they attempt to visit the site. Behind it, the WayBackMachine offers a view of what the site looked like before it was seized.
Investigating 37 Associated Domains Uncovered by WhoisXML API 🔗︎
Our friends at WhoisXML API performed a fantastic investigation. They uncovered over 35 additional domains associated with presstv[.]com, based on Whois data, some of which were still displaying live content at the time of their publication.
We will attempt to find additional domains and websites associated with presstv[.]com, starting with the 37 domains uncovered by WhoisXMLAPI. You can check their article in case you are curious about how to use Whois data for this type of investigation.
Download and watch our joint webinar with WhoisXML API now!Want to see this investigation in detailed step-by-step? 🔗︎
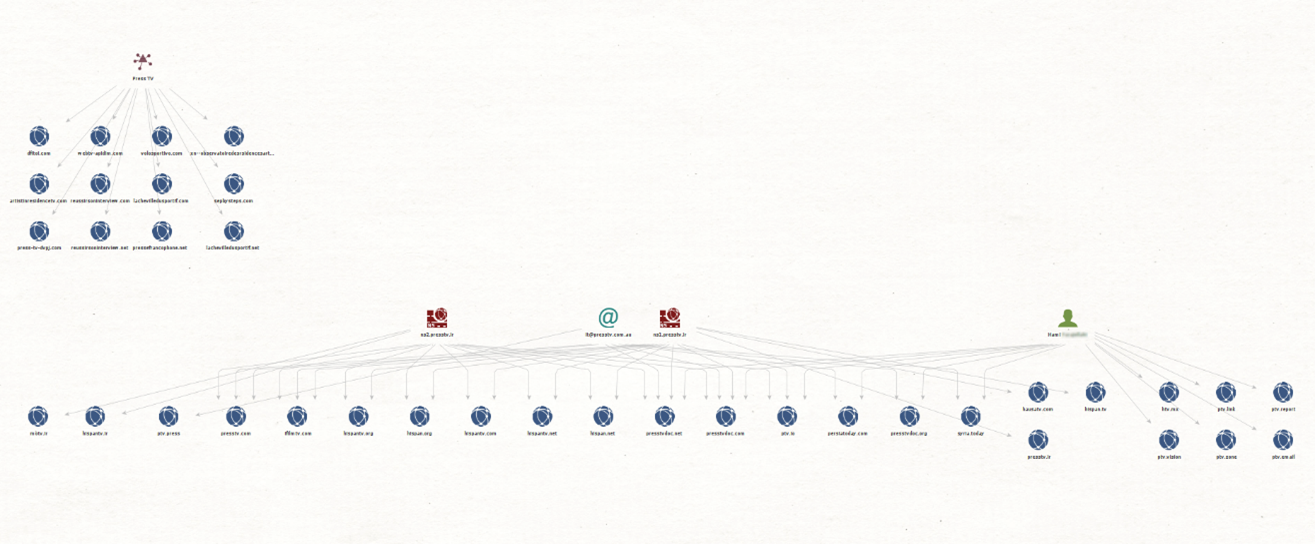
In the Maltego graph below, you can find domains uncovered in their investigation.
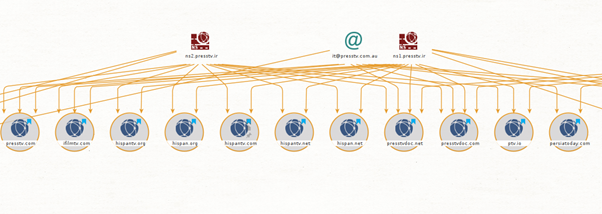
This image shows multiple domains sharing two nameservers (ns1.presstv.ir and ns2.presstv.ir) and an email address (it@presstv.com.au) linked to presstv[.]com.
Next, the image below shows a few domains registered by a person (Hami xxxxxxxx) who registered presstv[.]com. It is not clear from the domain names what company owns them. In contrast, in the case of presstvdoc[.]com or hausatv[.]com, where the name of the company is also the domain name, it is safe to assume that these are used to share information or TV-related content matching that of the original site.
We also got a few additional domains linked to an organization called “Press TV”. This was entered as the organization when presstv[.]com was registered.
Before we start our investigation, let’s bookmark our initial domains so that we can easily separate them from the rest once we are done. We will use a blue bookmark in this case, but you can use any other color.
We have a couple of options to select the domains on our graph, either by manual selection or using the “Select by Type” feature on our toolbar. We can then zoom into any of the domains and click the bookmark icon in the upper right corner of the Entity, which will automatically assign the same bookmark to all the other domains.
Next, We will simplify our graph with the help of the Collections feature. Moving the Collections slider all the way to the left decreases the number of Entities required to create a collection, which, in turn, forms collection nodes on our graph.
Pinpointing Websites Associated to the Known Domains 🔗︎
Let’s start by searching for websites associated with these domains. We have a couple of Maltego Standard Transforms available to do that:
- To Website using domain [Bing]: Leverages the Bing API and searches for any website that contains the domain as part of the URL.
- To Website [Quick lookup]: Adds a “www.” in front of the domain name and attempts to resolve it.
We decided to run both because they use different techniques to find websites related to domains.
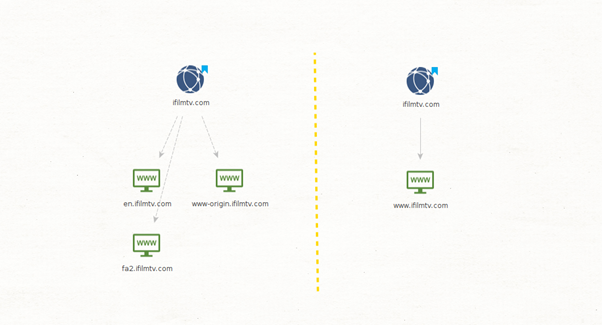
Below is a clear example of why running both gives us better results. On the left are the results of running the To Website using domain [Bing] Transform, and on the right are the results from the To Website [Quick lookup] Transform on the ifilmtv[.]com domain.
Use BuiltWith to Uncover Unknown Website Relationships 🔗︎
For the next step in our investigation, we will select the new websites and run the To Relationships [BuiltWith] Transform, which returned over 40 different Builtwith Relationship Entities.
From the results, we can see a combination of IPs and tracking codes (Alexa, Google-tag-manager, Google-analytics, etc.). The IP Entities contain information about IP Addresses used by the website and additional details such as when the IP was first and last seen by the site according to BuiltWith’s records.
In addition to IPs, we have tracking codes, which are small snippets of code usually implemented as JavaScript in the source code of a website. Tracking codes allow advertisers, web admins, and marketers to analyze the flow of visitors to websites and how they interact with different pages.
Tracking codes are fundamental for our investigation as we can use them to find other websites owned or managed by the same organization and further connect them with confidence since these codes are unique to different organizations.
Since we are only interested in the tracking codes, we can safely remove the IP Entities.
We can now select the remaining BuiltWith Entities, which should contain only tracking codes, and run the To Websites [BuiltWith] Transform. This will return other websites where the same tracking code has been used and might lead us to uncover previously unknown domains closely related to presstv[.]com.
As you can see below, we found 30 new websites. To make the results more readable, we will share them in two separate screenshots below.
The first part of the results shows multiple websites linked to ifilmtv, which, based on the subdomains (.en, .ar, .fa, .french), are probably versions of the same website but presented in different languages.
The second part contains a mix of domains, some related to presstv and hispantv, and we also found a few previously unknown and interesting websites like iranneshanclub.ir, dkdlab.com, iktv.ir, and sahartv.ir. This is why tracking codes are so valuable for uncovering hidden links between websites.
Map Out Correlations between Domains 🔗︎
Next, we will extract the domain names from the sites, as this will allow us to visualize the connections between some of the new websites by pointing them to the domain they are associated with.
Let’s select the website Entities and run the To Domains [DNS] Transform. Before we do that, we will also move the input websites to a new graph to make it easier to understand the latest results from each Transform.
We can see that around half of the websites point to unique domains, while the other half share a handful of domains. We also have three sites that did not return any results.
Using the bookmark colors to differentiate the confidence we have in our results (Green=High, Yellow=Medium, Red=Low), we bookmarked these new domains green.
We can now move the Entities back to the original graph with the standard CTRL+C and CTRL+V command.
Below is an extract of the results from merging the Entities with those already present in the Graph.
Tying the Links with Mail Servers (MX) 🔗︎
Another great piece of infrastructure that we can use both for uncovering additional domains and for tying the links between our previous findings are Mail Servers (MX).
Mail Servers or MX are used for processing emails and usually sit inside an organization’s infrastructure as the information processed by these is highly confidential.
Luckily for us, there is a Standard Transform that checks for MX Records, the DNS representations of Mail Servers. Below is the result of running the To DNS Name - MX (mail server) Transform on all the Domains, we also moved them into a separate graph for ease of readability.
We can see that most of the domains point to mail servers hosted on their infrastructure based on the mail server names, but there are 11 that point to email service providers such as OVH. These email service providers usually handle hundreds of customers who may be sharing the same infrastructure.
We are only interested in the mail servers hosted on their infrastructure as these reduce the chance of getting irrelevant results from our next step.
Let’s now select the MX records, and we will exclude the below ones since we suspect them to be email service providers.
- smtpin.rzone.de
- mail.h-email.net
- mx.hover.com.cust.hostedemail.com
- mx3.mail.ovh.net
- mx4.mail.ovh.net
We will then run the To Domains [Sharing this MX] Transform on the remaining ones, which, as shown below, returned 31 additional domains.
We will bookmark the newly discovered domains with a yellow flag since we have a high confidence in these being owned and used for the same purpose as the initial domains, but we should take additional steps to confirm our findings.
As we can see, the new domains share the mail servers with irib[.]ir, which after a quick Google search we confirmed to be the Islamic Republic of Iran Broadcasting (IRIB).
Examining Other Relevant Top-Level Domains 🔗︎
We have uncovered 41 additional domains so far, but we can take one extra step to find more domains.
We have observed the organization/group behind these domains consistently using multiple Top-Level Domains (TLD), such as (.com, .net, .ir, .org, .tv, .in, .us, .mx). This is sometimes leveraged by companies to have different websites serving specific audiences but is also a way to circumvent sanctions or restrictions.
A good example of TLDs being used to target specific regions or audiences for legitimate purposes are the apple.com and apple.cn websites.
But, if you are familiar with this case, you know that after the US Government seized the presstv[.]com domain, there was a new one presstv[.]ir that took its place in a matter of hours and started serving the same content as the one that was taken down.
Let’s check if we can uncover additional domains registered with other TLDs. We will once again move our Entities to a new graph before running the Transforms, so that we can easily understand the results. This also allows us to see how the bookmarks help us differentiate between our original domains and the ones we have uncovered so far.
We will select our domains one more time and run the To Domain (Find other TLDs) [WhoisXML] Transform, which looks for domains with the same name as the input, registered under different TLDs.
We have found 360 additional domains by running the last Transform, to make it easier to read, we will split the results into two separate images.
Before moving these domains back to our original graph, we will first bookmark them red (low confidence).
We will have to spend additional time on these if we want to confirm their relationship with our initial servers.
Let’s look at our final graph. As you can see, it has substantially grown thanks to all the domains discovered throughout our investigation in which we used only Maltego Standard Transforms.
Real-Life Investigation Using Maltego and OSINT 🔗︎
We hope you enjoyed this article and that the techniques used here serve you well in your future investigations.
As your next step, you can watch our live session with WhoisXML API, where we take an even deeper look into these websites and connections between them using the capabilities of Maltego and historical WHOIS data from WhoisXML API live.
Download the resource
Don’t forget to follow us Twitter and LinkedIn and sign up to our email newsletter to stay updated on new use cases, tutorials, and event information!
Happy Hunting!
About the Author 🔗︎
Mario Rojas 🔗︎
Mario Rojas is a Cyber Security Subject Matter Expert at Maltego with more than eleven years of experience in the cyber security field, specializing in risk management and threat analysis and is known for creative solutions that stem from his expert technical knowledge.





![Maltego imgae - a few domains registered by a person who registered presstv[.]com](/images/uploads/iranian-misinformation_4.png)



![run the To Relationships [BuiltWith] Transform in Maltego](/images/uploads/iranian-misinformation_10.png)


![run the To Websites [BuiltWith] Transform in Maltego](/images/uploads/iranian-misinformation_15.png)

![run the To Domains [DNS] Transform in Maltego](/images/uploads/iranian-misinformation_17.png)



![run the To Domains [Sharing this MX] Transform in Maltego](/images/uploads/iranian-misinformation_21.png)
![new domains share the mail servers with irib[.]ir](/images/uploads/iranian-misinformation_22.png)


![run the To Domain (Find other TLDs) [WhoisXML] Transform in Maltego_1](/images/uploads/iranian-misinformation_25.png)
![run the To Domain (Find other TLDs) [WhoisXML] Transform in Maltego_2](/images/uploads/iranian-misinformation_26.png)






