Founded by AlienVault (now AT&T Cybersecurity) in 2012, the Open Threat Exchange (OTX) offers a place for thousands of threat researchers and security professionals to share and discuss the latest threats and the indicators linked to them. With more than 140,000 participants from 140 countries, OTX receives more than 19 million indicators daily. We are bringing that power to Maltego for free! This blog post will take you on a tour of the new AlienVault OTX Transform Hub item.
About AlienVault OTX 🔗︎
One of the main features of OTX is its horizontality: Everyone can participate in the discussion and submit indicators. OTX users can upload indicators by creating a pulse. A pulse links a collection of indicators to a threat. To create a pulse, OTX provides its users with an extraction tool to run on documents such as a webpage or a PDF report but also from more industry specific sources like STYX or OpenIOC.
How to Access AlienVault OTX Transforms in Maltego 🔗︎
Most of the AlienVault OTX Transforms are available for all Maltego users and do not require an API key, except for Transforms for pulse lookups. However, registration to the API key is free!
All you need is a couple of minutes and an email address. After registering, you will be given an API key, which is required to fully exploit the OTX Transform Hub item. Sign up for an account here: https://otx.alienvault.com/
After doing so, install the AlienVault OTX item in the Maltego Transform Hub. After entering your API key, wait for the installation to finish, and you will be ready to unleash the power of OTX on your Maltego graphs.
Using AlienVault OTX Pulses via Maltego Transforms 🔗︎
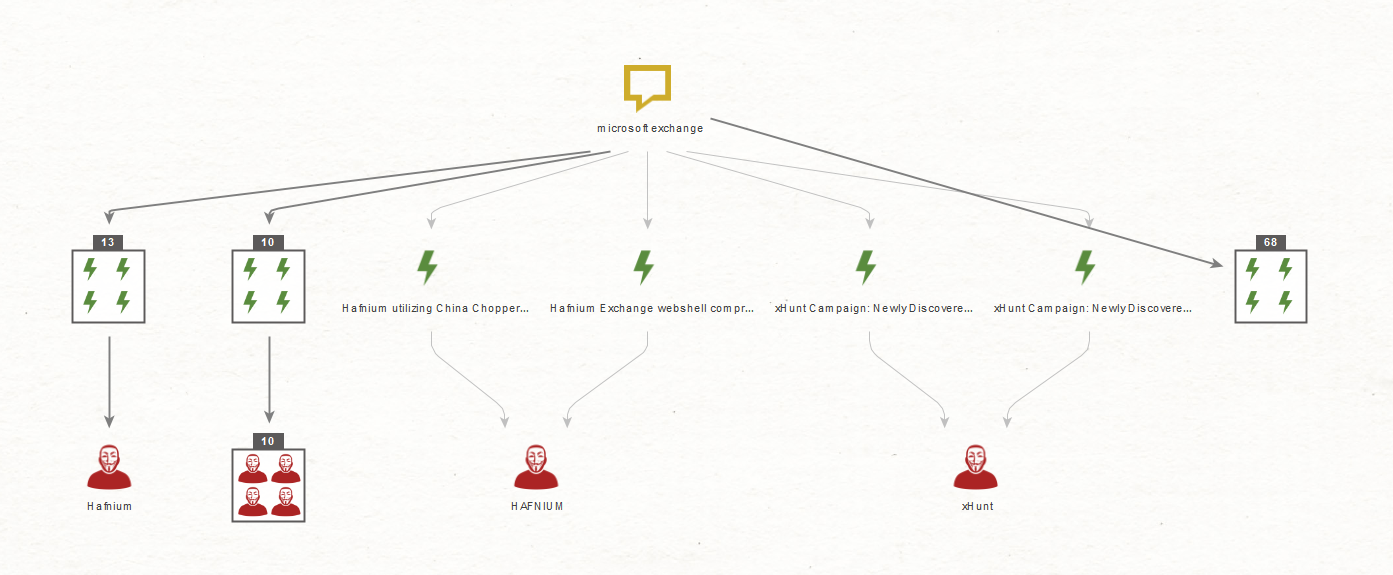
As stated before, you can search a pulse from different Entities such as a DNS name, an email address, a domain name, a hash, a CVE or even a Phrase Entity. For example, to investigate the Microsoft Exchange server hack, one would start from the Phrase Entity “microsoft exchange” and gather related pulses using the Search Pulses [OTX] Transform.
This returns ninety-five pulses, as seen on the image above.
Each pulse can contain many IOCs, which would crowd the graph if they were all added to it. To choose from which pulses to source indicators, you will need to vet them according to your criteria. Maltego offers three Transforms to gather data about the pulses:
- To Tags [OTX]
- To Adversary [OTX]
- To References [OTX]
The first Transform To Tags [OTX] returns the tags added by the pulse author, which convey general information about the pulse, such as the victim’s name or the malware family to which belong the hashes linked to the pulse.
When creating a pulse, OTX contributors can associate it with an adversary. It is possible to retrieve this adversary on the graph by using the To Adversary [OTX] Transform as shown in the image below. This allows you to focus your investigation on a particular threat actor.
Finally, the To References [OTX] Transform brings the URL of the source from which the pulse was created to the graph. Because the creation of a pulse is the result of a semi-automatic process, it is best to check that its source is trustworthy and that it is only aimed at the threat that the pulse is focusing on. This will save you from polluting your graph with IOCs unrelated to your investigation.
Retrieving IOCs from Pulses 🔗︎
Pulses can be expanded to add the IOCs they contain to your graph. You can use the To All Indicators [OTX] Transform to do so. You can also opt for a more granular approach by choosing which kind of IOC to add to the graph.
There are currently eight types of IOCs that can be obtained from an AlienVault OTX pulse:
- CVE
- Domain
- Email Address
- Hash
- Hostname
- IPv4
- IPv6
- URL
You will find a link to the OTX website in the Detail View panel of each IOC Entity, as highlighted on the picture below, which will provide more information about that particular IOC.
On the same picture, you will notice the “Date Observed:2020-11-10T06:40:55” label on the left. Several OTX Transforms store valuable information in the link label. To avoid missing any information, it is better to display custom link labels in your Maltego Client. You can do so by checking the “Show Custom Link Labels” as shown in the picture below.
Network Infrastructure Investigation Using AlienVault OTX Transforms 🔗︎
A big benefit of the current OTX Transforms is that typical Maltego use cases are centered around domain investigations and footprinting. Many possibilities are offered to the user to pivot from a domain or an IP address.
Instead of listing them, we prepared several short use cases showcasing these Transforms and how they can be of use in an investigation.
Use Case 1: Looking at University of California, Berkeley 🔗︎
In this use case, we will examine the domain of UC Berkeley and try to map its subdomains as well as the domains linking it.
Let’s start with the domain name of Berkeley (berkeley[.]edu) and look for subdomains using the To Subdomains (Passive DNS) [OTX] Transform. The OTX Transform returned several DNS records belonging to berkeley[.]edu and a few websites.
To find out the domains linking to berkeley[.]edu and its subdomains, we need to extract the domain names from the DNS records and the websites on the graph. We can do so by running the To Domains [DNS] Transform on the DNS record and the Website Entities on our graph. This Transform will return the domains contained in the DNS record while excluding the top-level domain and the second level domain, i.e. running it on the Website Entity www.its.berkeley[.]edu will add the Domain Entity its.berkeley[.]edu to the graph.
After running the Transform, it appears that the numerous DNS records on our graph belong to a handful of domains.
The last step is to find domains hosting a web page containing a link to berkeley[.]edu or one of its subdomains. Two Transforms are available to do so:
- To Linking Domains (Whois) [OTX]
- To Linking URLs (Whois) [OTX]
These Transforms will add to the graph the domains or the URLs belonging to these domains that contain a link to the input Domain Entity. After running these Transforms, we get the following graph:
Amongst the linking URLs, there are some expected results such as hxxps://moz.com/top500 (a website listing important domain names) or URLs belonging to the berkeley[.]edu domain but also some unexpected ones like hxxp://server.coolmakeupgames.com. These Transforms exploit data previously harvested, meaning that the domain or the webpages returned by these Transforms may be inaccessible by the time you run the Transform.
If needed, we can gather more information on a specific DNS name. Let us focus on one already present in our graph: “swarm-ewh-prod.devlib.berkeley[.]edu”. Via the To IP Addresses (Passive DNS) [OTX] Transform, the IP addresses linked by this DNS record are added to our graph. Then, focusing on the most recent one, we can extract the opened ports and the banners observed on that IP using the To Ports [OTX] and To Banners [OTX] Transforms.
Use Case 2: Examining BitCoin Miners 🔗︎
In this use case, we will explore a pulse related to BitCoin miners: https://otx.alienvault.com/pulse/604d22edf53617b73d56428c
By sorting the IOCs by roles, it appears that two IP addresses are categorized as C2. For this investigation, we will focus on one of them: 209.202.252[.]54.
After adding this IP address to our graph, we check if there are any DNS records attached to it by running the To DNS records (Passive DNS) [OTX] Transform. This returns one DNS records observed for that IP address: ftp.tripod[.]com. This domain belongs to a web hosting company, meaning that it is most likely not where the C2 is housed and that the command & control servers are possibly hosted on a subdomain, which is rented to its customer by the company.
To obtain the subdomains of tripod[.]com, we proceed in a similar manner as the last use case: On the DNS records gathered using the previous Transform, we run the To Domains [DNS] Transform. And on the returned Domain Entity “tripod[.]com”, we run the To Subdomains (Passive DNS) [OTX] Transform. This gives us a few hundred DNS records Entities.
To get further information, we pull the IP addresses linked to these DNS records using the To IP Addresses (Passive DNS) [OTX] Transform. The first observation that can be made is that a lot of these domains are hosted on the same server. There are almost three hundred DNS records on our graph, and they are only pointing to fourteen different IP addresses.
Now that we have the IP addresses of these DNS records, we can search for malware linked to these IPs by running the To Malware Hashes [OTX] Transform. This Transform will return the hashes belonging to malware analyzed by AlienVault that has been observed connecting to this IP.
It appears that five IP addresses are linked to malware hashes. We also observe that the majority of the domains linked to these IP follow a particular naming convention: “logsamk” + X + “.tripod[.]com”, X being a number between 0 and 300.
Thanks to the labels of the links between the IP addresses and the hashes (see image below), we notice that these pieces of malware have been observed at some very different time intervals: Some date from early May 2021 while others were first spotted in 2016! This could indicate that different threat actors are using these domains or that they were part of different campaigns.
To be able to understand the global picture at a glance, we can order the hashes by date of observation by bookmarking them: Samples from 2021 in blue, late 2020 in green and everything else in yellow. After doing so, we obtain the graph below.
Start Using the New AlienVault OTX Transforms in Maltego! 🔗︎
We hope that this glimpse of the AlienVault OTX Transforms got you excited!
It should be noted that the Transforms presented in this blog article only make use of a fraction of the possibilities offered by OTX. New Transforms are to come to exploit the full potential of OTX in Maltego, so stay tuned for incoming updates by following us on Twitter and LinkedIn and sign up for our email newsletter.
Happy threat hunting!


 4.5 rating
4.5 rating